Management Approach
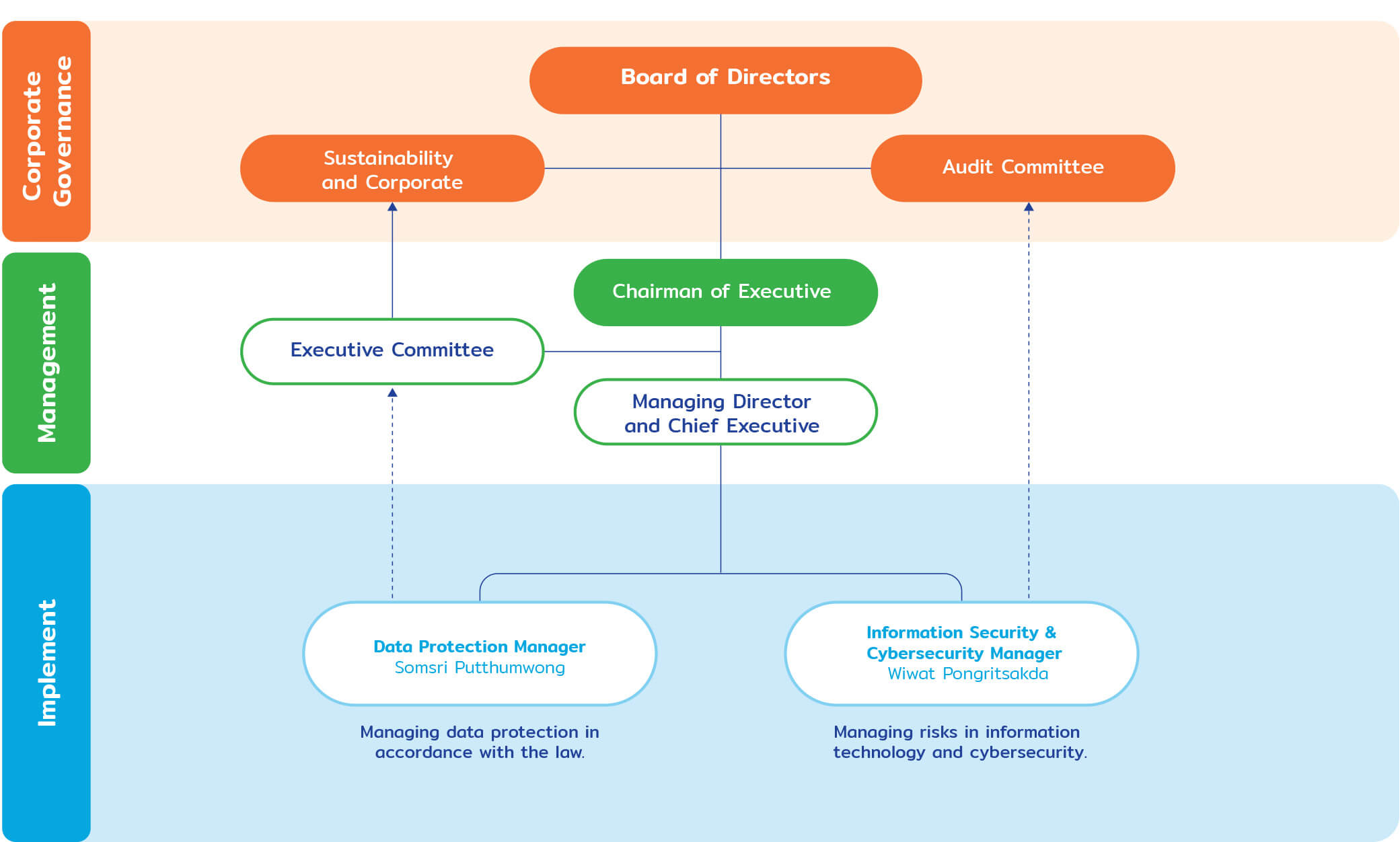
Information Security & Cybersecurity Structure Committee
CP All Plc. and its subsidiaries (“the Company”) give importance to continuous development and strengthening of businesses, with the use of information technology and cyber widely. It is to increase effectiveness and efficiency of products and services, including internal work system improvements from the communication infrastructure both inside and outside organization, collecting and gathering data throughout the business chain, production and transportation planning, increasing productivity in factories, quality control of the production process, increasing the quality of service before and after the sale, maintenance, etc. Employees will have their own User Account in order to access the system and services of the organization according to the rights and necessities related to the operation and to ensure the use of information technology and cyber security. The organization has issued a policy regarding Information Technology (IT Policy) as a guideline for data usage, operations, development, and maintenance of information technology systems appropriately comply with laws and relevant security requirements for both employees and business partners. Furthermore, the organization has also utilized the standardization and certification in the provision of quality information technology services, namely ISO 20000 and the implementation of the certified standards for safe information technology management, ISO 27001, as a framework for operations in the area of information technology and cyber administration and the security standards for financial transactions which is PCI / DSS V.3.
The Company has set up a management structure for integration from the center and business groups, with a central unit bearing and providing support the working groups consisting of the IT Governance Committee which is responsible for establishing policies and guidelines for the use of the monitoring system for information technology and cyber investment projects in the same direction and in accordance with business strategies.
Information Technology and Cyber Risk Management
The Company has adopted the risk management principles by having the risk monitoring committee and risk management team in managing information technology and cyber risk. In addition to assessing the risks from the Company’s activities, the Company also surveyed cyber threats of other organizations, both in the same and different industries, in order to learn and assess the potential risk that may occur to the organization and can also cause damage to customers, stakeholders, and business partners.
Information and cyber security management measures
The Company is committed to developing and implementing information technology systems in order to maintain security and maintain confidentiality, Integrity, and availability of all information. The Company has established cyber security management measures as follows:
Principle
Cyber Security Management Measures of CP All Business Group
The Company has adopted the NIST Cybersecurity Framework as a cyber security framework and conducted risk assessments to prevent, detect, respond, and revise to keep data and information secure and ready to perpetually provide services.
Policy
The Company manages cyber security under the information security policies and practice guidelines which enforce CP All Plc. and its subsidiaries including directors, executives, employees, and authorized third-party service providers to access information at each level of everyone’s confidentiality.
Process
The Company has established an operating information department and nominated by top executive in order to manage the information system services and information security certifying by the IT service standards with ISO20000 and the information security management systems standards for Data Center, Bill systems with ISO27001 and All member systems with ISO27701 as well as the payment card industry data security standards for Payment Gateway Systems with PCI / DSS V3.0.
Technology
The Company has invested in a computer center that meets international standards, including a backup computer center that is ready to work immediately and requires storing important customer data and information within the said computer center under the design of zoning and access control for authorized persons only. For managing cyber threat risks, the Company has installed appropriate technologies to prevent, detect, stop, and alert as follows: Firewall, Intrusion Prevention System, Anti-Malware, Web & Mail Security, Threats Detect & Prevention System, Active Directory, Two-Factor Authentication, Privileged Access. Management, Patch Management, Security Information and Event Management (SIEM), including the making of Vulnerability Assessment and Penetration Testing in critical systems, either before services or when significant changes occur and in annually.
Personnel
There are trainings and testing to raise awareness and beware of Cyber Attack through Cyber Security Awareness and Cyber Drill for employees and executives at all levels. The Company also attaches importance to the security operation team by supporting and promoting training, testing to pass international standards certifications such as CISSP, CISA, CDPSE, C|HE (Certified Ethical Hacker) CompTIA Security+, as well as having a group of cyber practitioners, experts for advising, and business partners from both domestic and international that are engaged in working and overseeing related technical systems.
CP ALL Cyber Security Management
Daily operations and tracking
The Company has an IT Operation Team that is ready to work 24 hours a day at the main computer center, which is responsible for monitoring and supervising the system at all times, and users can report security incidents or others through Call Center 1500 staff at any time as well. The operations of the security team will operate through a process called Incident Management which is one of the ISO20000 work processes with levels of priorities and solutions programming. There will be notifications of intrusion or security breaches through the specified system, both automatically suppressing and notifying the system administrators to carry out the process of checking and fixing according to the specified procedures.
Data showing Cyber Attack reports in 6 years (2017 – 2022)
It is an external attack that slips out of automatically detection into the system by trying to access the system and important information through various techniques such as Phishing, Ransomware, Brute Force, Malicious Code, DDoS, etc. However, at the next level of protection, when the system administrators have received an unusual alert, they can go in and quickly fix the case that damages the system but is in control not affecting other systems and important information, which in this case is considered likely to occur, can be detected and resolved in time, without affecting the normal service.
Data showing User Security Incident reports in 6 years (2017 – 2022) It is a notification to the service provider (Call Service 1500) in accordance with the Incident Management procedure and can be resolved within a specified period (SLA), which is an unusual event from service user’s use such as forgot password, lost device, attempts to use the wrong code, and virus infection on the user machine.
Data showing a 12-months (01/01/2022 – 01/01/2023) report of automatic Cyber Attack detection that attempted to steal company network data, but the system can firstly stop and prevent data damage.
Threats for all my domains – Last 12 Months
6,792,470
Total
20,564
Phishing
0
Analyzed Advanced Threats (Files)
589
Ransomware
Data showing a 12-months (01/01/2022 – 01/01/2023) report of automatic Cyber Attack detection trying to break into the corporate network, where the system can firstly stop and prevent network damage.
Related Policy and Guideline
| Information Security Policy | Download |