Management Approach
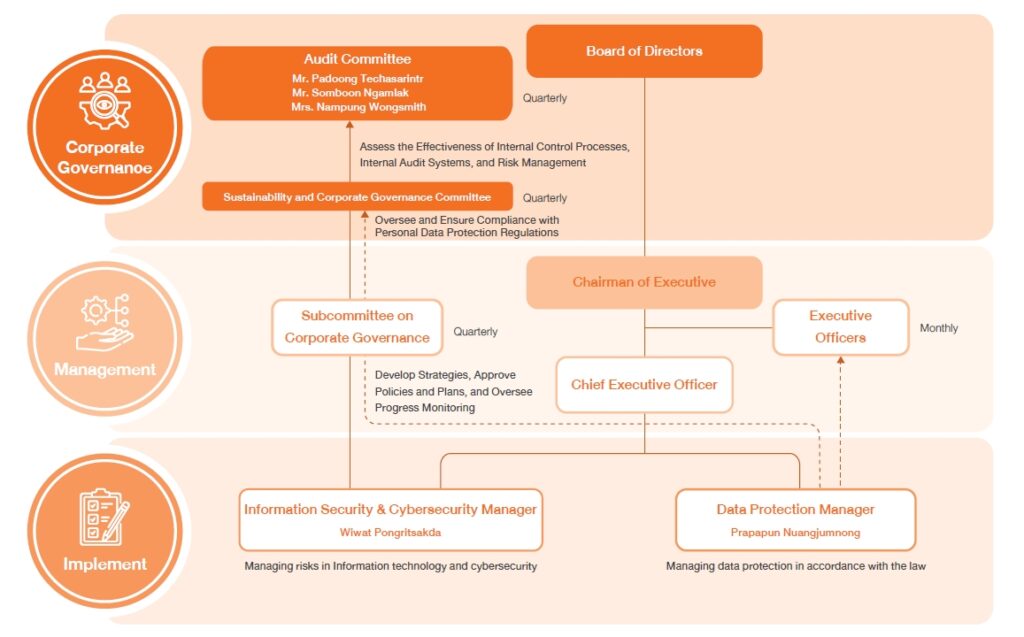
Information Security & Cybersecurity Structure Committee
CP All Plc. and its subsidiaries (“the Company”) give importance to continuous development and strengthening of businesses, with the use of information technology and and cyber security technology. It is to increase effectiveness and efficiency of products and services, including internal work system improvements from the communication infrastructure both inside and outside organization, collecting and gathering data throughout the business chain, production and transportation planning, increasing productivity in factories, quality control of the production process, increasing the quality of service before and after the sale, maintenance, etc. Employees will have their own User Account in order to access the system and services of the organization according to the rights and necessities related to the operation and to ensure the use of information technology and cyber security. The organization has issued a policy regarding Information Technology Policy as a guideline for data usage, operations, development, and maintenance of information technology systems appropriately comply with laws and relevant security requirements for both employees, partners and customers The company has been certified to various international standards such as ISO/IEC 20000 for providing quality information technology services, ISO/IEC 27001 for managing secure information technology, ISO/IEC 27701 for managing personal data, and PCI/DSS V3.1 for payment data security, etc..
The Company has set up a management structure for integration from the center and business groups, with a central unit bearing and providing support the working groups consisting of the IT Governance Committee which is responsible for establishing policies and guidelines for the use of the monitoring system for information technology and cyber investment projects in the same direction and in accordance with business strategies.
Information Technology and Cyber Risk Management
The Company has adopted the risk management principles by having the risk monitoring committee and risk management team in managing information technology and cyber risk. In addition to assessing the risks from the Company’s activities, the Company also surveyed cyber threats of other organizations, both in the same and different industries, in order to learn and assess the potential risk that may occur to the organization and can also cause damage to customers, stakeholders, and business partners.
Cyber Security Management Goals
The Company is committed to developing and implementing information technology systems that are secure, maintain confidentiality, integrity, and availability of all information, and comply with important IT legal requirements, such as the Personal Data Protection Act B.E. 2562, etc., by operating with the following management principles and practices:
Principle
Cyber Security Management Measures of CP All Business Group
The company has adopted the NIST Cybersecurity Framework as a global cybersecurity framework and conducted risk assessments to lead to preventive, detective, response, remedial, and restorative measures to ensure that data and information are secure and ready for continuous service.

Identify

Protect

Detect

Respond

Recover
Personnel creating an organizational culture with safe cyber hygiene
The Company places great importance on building corporate culture and cyber threat awareness, dividing the target groups into 4 groups:
Giving importance and following up from top executives
Information and cyber security training and awareness raising
Motivating with clear rewards and punishments
Measurement improves measures and promotes a consistent safety culture
Cybersecurity Management Guidelines
The company has managed cyber security with the goals set out above. by setting important guidelines And it is carried out through both promoting personnel at all levels to have safe cyber hygiene. Evaluating and controlling important work systems to meet the specified safety standards. and operations are carried out by a team of system administrators, both preventive, surveillance, and deterrence using appropriate technology Compatible with business environments And cyber threats constantly changing
Cyber Hygiene Culture
Cyber Assurance

Cyber Operation
The above activities are carried out through the following personnel, processes and technologies:
People
Process
Technology
Policy
The Company manages cyber security under the information security policies and practice guidelines which enforce CP All Plc. and its subsidiaries including directors, executives, employees, and authorized third-party service providers to access information at each level of everyone’s confidentiality.
Process
The Company has established a unit for information and cyber security operations and management, with a Chief Security Officer and a Data Protection Officer directly responsible. Information system and information security services are certified to international standards.
As follows: ISO/IEC 20000 Information Technology Service Standard, ISO/IEC 27001 Information Security Management Standard, ISO/IEC27701 Personal Data Management Standard, and PCI/DSS V3.1 Payment Security Standard, etc.
Technology
The Company has invested in a computer center that meets international standards, including a backup computer center that is ready to work immediately and requires storing important customer data and information within the said computer center under the design of zoning and access control for authorized persons only. For managing cyber threat risks, the Company has installed appropriate technologies to prevent, detect, stop, and alert as follows: Firewall, Intrusion Prevention System, Anti-Malware, Web & Mail Security, Threats Detect & Prevention System, Active Directory, Two-Factor Authentication, Privileged Access. Management, Patch Management, Security Information and Event Management (SIEM), including the making of Vulnerability Assessment and Penetration Testing in critical systems, either before services or when significant changes occur and in annually.
Personnel
There are trainings and testing to raise awareness and beware of Cyber Attack through Cyber Security Awareness and Cyber Drill for employees and executives at all levels. The Company also attaches importance to the security operation team by supporting and promoting training, testing to pass international standards certifications such as CISSP, CISA, CDPSE, C|HE (Certified Ethical Hacker) CompTIA Security+, as well as having a group of cyber practitioners, experts for advising, and business partners from both domestic and international that are engaged in working and overseeing related technical systems.
Information Security Controls and Practices
CP ALL Public Company Limited prioritizes cyber risk management to ensure business continuity even amidst cyber threats or attacks. The Company has developed a comprehensive Business Continuity Plan (BCP) that is seamlessly integrated with the Disaster Recovery Plan (DRP) and the Incident Response Plan (IRP).
All plans are designed to operate cohesively within an Incident Management Process to address and minimize the impact of system attacks or IT disruptions. The DRP is tested at least once annually, and both the BCP and IRP are continuously reviewed and updated.
Furthermore, the Company implements stringent security measures and risk controls to ensure ongoing business operations and compliance with relevant legal requirements, such as the Personal Data Protection Act (PDPA), and international cybersecurity standards like the NIST Cybersecurity Framework (NIST CSF).
CP ALL Public Company Limited places paramount importance on its ability to maintain continuous business operations, even in unexpected situations. We’ve developed a comprehensive Business Continuity Plan (BCP) that covers significant events potentially impacting operations and information security, both physical and cyber. These include:
1) Blackout or Fire Incident
The company has clear guidelines and procedures to respond to emergencies such as power outages or fires, which could affect critical services or systems. Our measures include:
These guidelines are designed to limit impact, protect lives and assets, and ensure continuous business operations.
2) Information Security Threats
The company has established an Information Security Incident Response Plan (IRP), systematically integrated with our BCP and DRP. This plan addresses threats related to information systems, such as ransomware attacks, data breaches, unauthorized access, or service disruptions. Our practices include:
These practices reflect our commitment to maintaining information security, building trust, and strictly adhering to legal requirements.
CP ALL continuously monitors and assesses information security risks across various dimensions. This proactive approach helps prevent cyber threats and ensures service reliability. Our practices cover general systems, critical business systems, and internet-facing systems, as outlined below:
1. Vulnerability Assessment
We conduct automated and continuous scanning and assessment of vulnerabilities across all systems. In 2024, the overall assessment result was a “C” grade (on an A to F scale). Relevant departments actively monitor, track, and remediate high-risk vulnerabilities to ensure system security and continuous service.
2. Penetration Testing
Critical business systems must undergo security penetration testing before deployment. This is performed in collaboration with third-party experts to identify and close potential exploitable vulnerabilities. In 2024, we conducted application penetration tests on a total of 20 business-critical systems.
3. Security Rating
The company’s internet-facing data and service websites are assessed by an independent provider, Bitsight Service. This involves vulnerability detection, analysis, and risk assessment for over 250 IP addresses across the organization. The 2024 assessment result was 780 points (Grade A), exceeding the international average of 730 points. This reflects our good security posture and effective control.
CP All Public Company Limited places importance on information technology management and data security across all relevant processes. The company operates in accordance with accepted international standards to enhance confidence in both internal and external services, and to ensure IT operations comply with relevant standards, policies, and laws. Therefore, regular internal audits are conducted.
Internal Audits are conducted twice a year: the first in April and the second in September. These audits are performed under the scope of ISO20000, ISO27001, and ISO27701 standards, covering a total of 53 IT services.
1. ISO20000 standard scope: 10 items
2. ISO27001 and ISO27701 standard scope: 2 items
These issues primarily relate to outdated documentation.
CP ALL Public Company Limited places significant importance on the management of Information Technology (IT) and Information Security across all related processes. We adhere to recognized international standards to ensure confidence in our services, both internal and external.
The company have engaged expert consultants and external auditing bodies to continuously review, assess, and provide recommendations for improvement. This commitment has led to the following key certifications:
ISO/IEC 20000: IT Service Management Standard
This standard covers the Company’s internal IT service units. We undergo annual assessments and re-certifications to ensure our IT services are efficient, support continuous business operations, and professionally meet user needs.
From the latest audit results in May 2025, 2 recommendations for improvement were found.
ISO/IEC 27000: Information Security Management Systems Standard
This standard encompasses the Company’s critical systems, including the IT Operations & Computer Center, Bill & Payment system, All Member customer and loyalty program data, 24Shopping online sales platform, and the Human Resources Information System (HRIS). This certification ensures that our security controls are comprehensive and effective at an organizational level.
From the latest audit results in May 2025, 3 recommendations for improvement were found.
ISO/IEC 27701: Privacy Information Management Systems Standard
This standard covers systems involved in the storage, processing, and management of customer and employee personal data, such as the Bill & Payment system, All Member customer and loyalty program data, 24Shopping online sales platform, and the Human Resources Information System (HRIS). Our practices strictly adhere to personal data protection principles and comply with relevant laws, including the Personal Data Protection Act (PDPA).
All employees and users can report suspicious incidents or information security issues through the company’s designated channels: Hotline Calls: 02-071-1500, 02-826-7733, Email to the Data Protection Officer: privacy@cpall.co.th, Email to the Cybersecurity Administrator: itsecurity@gosoft.co.th.
All received information will be recorded in the Incident Management System and escalated to the responsible departments, including the Information Security Management team, for urgent investigation, analysis, and resolution.
Once an incident is resolved, we’ll follow post-incident procedures as per the defined plan. This includes creating follow-up reports and conducting lessons learned meetings to prevent recurrence.
Cybersecurity Management Performance Results for 2024
| Topic | Target | Number of target groups | Percentage |
|---|---|---|---|
| Cybersecurity Awareness Training | Store Employee, Office | 116,179 Persons | 100% |
| Cybersecurity Engineer Training | Security Administrator | 31 Persons | 100% |
| Cyber Drill Test | Office | 10,388 Persons | 100% |
| Incident Response Plan drill | Executive | CMC, BIRT, CSIRT Team | 100% |
| Topic | Industry average | Score |
|---|---|---|
| Cybersecurity Self-Assessment By CPG | 88% | 91% |
| Cybersecurity Resilience Survey By SET | 1.71 (1.0 – 5.0) | 3.52 |
| Security Rating By BitSight Service | 730 (100 – 900) | 780 |
The Company has conducted a cyber risk assessment based on the NIST Framework and has taken action to enhance its outstanding cyber security in 2024 as follows:
| No. | Process | Outstanding Information Security and Cyber Security Projects in 2023 |
|---|---|---|
| 1 | Identify | The Company conducts annual Cybersecurity Gap Analysis against international standards, specifically NIST 2024. The key findings from this assessment are as follows:
|
| 2 | Protect | The Company enhances its secure software development lifecycle from the outset, leveraging technology to mitigate emerging vulnerabilities that pose potential cyber threats. This includes:
|
| 3 | Detect | The Company enhances its Security Operation Center (SOC) by leveraging AI technology to analyze cybersecurity incidents and monitor data leaks. This involves continuous surveillance for unauthorized data exposure or disclosure, which can result from cyberattacks or internal security negligence |
| 4 | Respond | The Company continuously prepares for abnormal situations by conducting regular incident response drills, simulated attacks on critical IT systems, ransomware scenarios, personal data breaches, and communication tests. This also includes ongoing employee phishing simulations test throughout the year |
| 5 | Recover | The Company maintains a comprehensive business-critical system backup and recovery plan, with scheduled testing of both the systems and the relevant operational teams |
The number of complaints received regarding personal data breaches and data loss
| Indicators | Target | 2024 |
|---|---|---|
| Total number of information security breaches | 0 | 0 |
| Total number of clients, customers and employees affected by the breaches | 0 | 0 |
Related Policy and Guideline
| Information Security Policy | Download |
